Email Strategy
Published November 25, 2013 01:28
I've seen a few different articles about people's different e-mail strategies and they certainly seem to be a hot topic. With our ever reliance on e-mail as a primary mechanism for communication it's important to be able to keep up with the constant stream of messages coming in. You ultimately have to devise a strategy that works for you, and there are many out there already, I'll be throwing my hat into the ring. To sum up my strategy, stop organizing, start searching and use flags to make s...
I’ve seen a few different articles about people’s different e-mail strategies and they certainly seem to be a hot topic. With our ever reliance on e-mail as a primary mechanism for communication it’s important to be able to keep up with the constant stream of messages coming in.
You ultimately have to devise a strategy that works for you, and there are many out there already, I’ll be throwing my hat into the ring. To sum up my strategy, stop organizing, start searching and use flags to make sure nothing slips through the cracks.
Here are a few of the strategies that I’ve tried historically and why I’ve decided they don’t work for me. Ultimately I’m an Occam’s razor kind of guy, so I try to stay away from complexity.
- Inbox Zero - I have too many items that need more a day to process and I don’t like feeling guilty about todo messages. I don’t have an easy way to archive and search through the archive, however I use a lot of tactics from I0 with my strategy using Flag For Follow-up.
- Labels/Folders - I’ve tried folders, but folders assume that I know how I want things to be organized before the messages come in. I’ve tried organizing by client, by project, etc. but it always falls apart. I also have to remember to organize them as they’re coming in.
- “Getting Things Done“ - This is more of a time management strategy, but it could be applied to e-mail as well. It’s too complicated for a messaging system.
Here’s my detailed strategy: I don’t really use folders or filters, other than spam, github and mailing lists (which are all kind of the same thing). Those go into their respective folders and I almost never look at them.
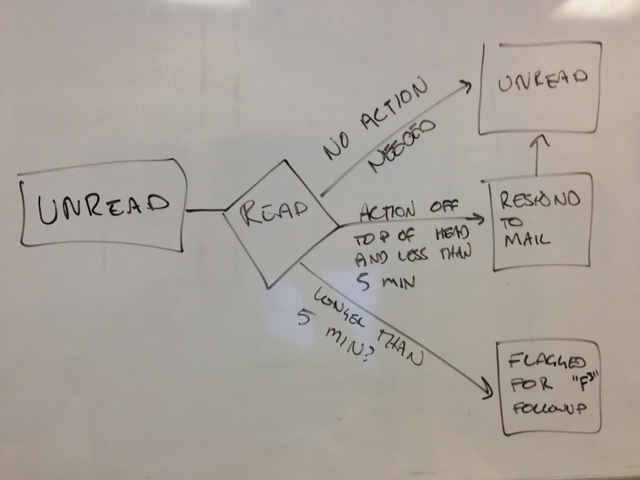 My e-mail is generally in three states: unread, flagged, read, and it all stays in the inbox. Then I use searching to find stuff later.
My e-mail is generally in three states: unread, flagged, read, and it all stays in the inbox. Then I use searching to find stuff later.
- Unread - I haven’t read it (also may mean I’ve read it on my phone, but requires action since flagging doesn’t work on the iPhone properly, this will be taken care of or flagged when I get to my computer)
- Flagged For Follow Up (F^3) - I need to take some action that will take more than a couple minutes to respond to.
- Read (and not flagged) - no action needed at this point (essentially archive).
There’s one other flag I use “Informational” which is for e-mails that I need quick reference to, but don’t need my attention any more.
In the morning I plow through all e-mails. I read them all quickly. Respond to anything I can off the top of my head. Anything that takes longer than a few min to respond to I’ll flag it for follow up. Once I get through my inbox I start tackling my flagged box.
If it’s time sensitive (needs a response quickly), but won’t take too long to follow up, I do those first. Then I’ll tackle the ones that are time intensive, but do require some time (or I need other people to help with). Finally I’ll take care of the ones that are time intensive.
If the F^3 folder gets into the double digits I carve out some time during the day to get it down and make a concerted effort to make sure there’s no cruft left over or somebody who has been waiting for my response for days.
 If I zero out my F^3 box and everything is “read” I send out an e-mail to folks letting them know that if they’re waiting for something from me that I’ve lost it. This only happens once or twice per year, but it’s an opportunity for me to alert anybody who thinks their request is still in the queue to remind me.
If I zero out my F^3 box and everything is “read” I send out an e-mail to folks letting them know that if they’re waiting for something from me that I’ve lost it. This only happens once or twice per year, but it’s an opportunity for me to alert anybody who thinks their request is still in the queue to remind me.
I go through this process a few times per day, but generally either stay in front of the mails as they come in by keeping mail up and running the whole day, or I shut it down to get work done that requires more focused attention then let them build up and start at the top again.
I use Mail.app for my mail with the GPG plugin and my SMIME Cert installed. I use the following mail settings to make it suck less:
This one will default to SMIME instead of PGP for encrypting and signing.
defaults write org.gpgtools.gpgmail DefaultSecurityMethod -int 2
The one will force attachments to be displayed in icon mode instead of view mode.
defaults write com.apple.mail DisableInlineAttachmentViewing -bool yes
I use a setting to highlight addresses not ending with @securityinnovation.com which will make any other domain show up red. This reduces the risk of sending SI sensitive information outside of SI.
I am adamant about adding images to each sender in my contacts list. This makes it easy for me to recognize anybody who is sending me email, which makes it easier to find the information I need.
I set mail to mark whether I’m on the to or cc line of e-mails, which is nice, but it doesn’t play into how I respond to e-mails because senders aren’t reliable enough with those fields.
Using this strategy I don’t have to search for e-mail much. Anything I need is right in front of me in my F^3 folder or it’s unread. That means I don’t waste time searching through folders or tags or labels.
I rely on Mail.app’s built in search index, which can be good, but it does struggle with 10,000+ messages to search through. It does a good enough job, though that I’m happy.
Since I rely on searching to find e-mail it’s important for senders to send me mail with good subject lines and content. If the mail gets read and isn’t flagged, and doesn’t have a good subject and body it may get lost. Maybe I’ll write another blog post on e-mail etiquette sometime, but for now this article describes How to Email Busy People
In case I don’t get to my version, here’s a sneak peak off the top of my head:
- Use Subjects - These are incredibly important to help sort and filter email mentally.
- Be concise - Send all the information needed and with recommendations on action in the first paragraph. If you need to support your recommendation, do that after and mark it as such. Example: “I’m increasing our weekly coffee purchases from 3 lbs per week to 7 lbs per week. If you’re interested why, or disagree, please read on…”
- Respect the Thread
- Reply to the right thread - Most modern e-mail clients build threading in. They either do this by subject or thread index or some other mechanism. Try to keep each conversation thread separate, even if you have multiple conversations going with the same person.
- One subject per thread - similar to above, but talking about multiple clients or unrelated issues in the same e-mail
- Break questions into lists - if you have multiple questions I have to answer in an e-mail, break them into lists. I can copy your questions and respond inline easily. This makes it easy for you to know that I’ve answered all your questions and makes it easy for me to do the same.
- Use my name if I need to do something - on its own separate line start with something like “Joe: Check on the widgets before Monday” I can quickly grab that todo item out of my mail and act on it. If you bury your ask in the middle of a paragraph I may forget and lose it.
- Use to, cc and bcc properly - I’ve almost given up on this, but if people could use the fields properly I think email could be more efficient.
Posted By: Joe Basirico
