Why You Should Have Trust Issues with Pokemon Go, and Every Other App on Your Phone
Published July 13, 2016 23:39
*Viral Game Highlights Calls Attention to Timeless Security Debate* I want to run into traffic, [fall into a pond](https://www.twitch.tv/i_play_too_much_gragas/profile), catch Pokémon while [my wife is in labor](https://imgur.com/gallery/bKhZiDo), and [find a dead body](http://money.cnn.com/2016/07/09/technology/pokemon-go-dead-body/); let's check out this Pokémon Go thing! Pop quiz: Is this a valid login screen for Google Account services? This is the first screen I see when I...
Viral Game Highlights Calls Attention to Timeless Security Debate
I want to run into traffic, fall into a pond, catch Pokémon while my wife is in labor, and find a dead body; let’s check out this Pokémon Go thing!
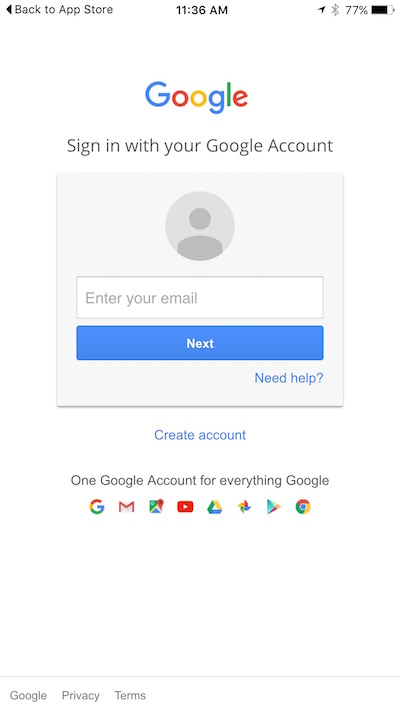
Pop quiz: Is this a valid login screen for Google Account services? This is the first screen I see when I click login with my Google Account from Pokémon Go. It’s concerning because it offers no clear indication this is a valid page, no way for me to verify that I’m sending my credentials to Google, no SSL/TLS lock, and no security controls – just a white page that looks pretty legit.
 Adam Reeve wrote a good post about this already. He’s not quite right about the access Pokémon Go requests, but the message that we should question the privileges we grant Pokemon Go, and every other application, is a good one to take to heart.
Adam Reeve wrote a good post about this already. He’s not quite right about the access Pokémon Go requests, but the message that we should question the privileges we grant Pokemon Go, and every other application, is a good one to take to heart.
Pokémon Go requests Full Account Access when you sign in using your Google account on an iOS device (note: it looks like they’ve issued a fix for the issue, but this would have been a good opportunity for them to catch this early with a 3rd Party Security Assessment). It’s hard to discover what “can see and modify nearly all information in your Google Account” means from that page, but we can all agree it’s more than we want Pokémon Go to have direct access to. As a security person, this is really scary.
It’s not just Pokémon Go, though. It’s every application you install on your device and use another account to log in to. The promise of only having to remember a single password is great, but it does put all of our proverbial eggs in one basket. In this case it’s a matter of making sure this app just requests the fewest permissions it needs to operate. But in others you may log in using your Facebook, Microsoft, Twitter, or any of the 62 other providers that are easily available. If you sign into one of these services you must first verify that you are signing into an OAuth provider – this protects your account credentials from being sent to the app developers; and second, you must check the requesting permissions of the application.
To make it even more complex, you should also verify that the permissions the app requests on your device itself don’t overreach. It’s not OK for my calculator app to know my location, or to be able to access my photos or camera.
My team’s motto is “We have trust issues.” We have shirts, mugs, and pint glasses with this on it, so I’ll admit I’m paranoid, but I’m also not ready to hand over everything that I use Google to manage to a random app dev.
This calls into question a timeless debate in the industry about the balance between security and privacy and features and fun. It’s fun to play Pokémon Go, it’s fun to integrate everything with everything. Hell, connecting first and worrying about the consequences later is a fundamental driving force of how the internet was created. That doesn’t mean that leaping before we look hasn’t gotten us into a lot of trouble though.
I’m the VP of Services at Security Innovation, and part of my job is helping to make security decisions for our company. I help decide if we’re going to allow a third party app or service to connect to our Google accounts.
Most of the time the answer to that question is no.
We live and work in a trust-based industry. One data breach or even the hint that we don’t keep our customer’s data perfectly secure and we’d deserve to be out of business.
We take this responsibility incredibly seriously.
Sometimes saying no because of security reasons means we can’t have fun things. We use a self-hosted feature restricted version of Slack for collaboration. No third party integrations and no mobile apps. What it does have is a small attack surface and easy to review code, and it lives on an internal, encrypted, locked down server within our complete control.
We have to think not only about the trust between us and the third party, but the trust we have with their developers, contractors, and security assessments, audits and personnel. We need to know beyond a doubt they will always act in our best interest.
There are few companies I would trust with our customer’s data; in fact the number of companies that I trust with unencrypted customer data is zero.
The biggest lesson we can all take away from this conversation is to think before we act. Think about the tradeoffs between features and fun and security and privacy. Is it reasonable that your flashlight app requests access to your photos? Is it right that the Flappy Bird knockoff needs your location information? Is it good that Pokémon Go needs full Google account access?
Posted By: Joe Basirico

